We support our clients in areas such as cybersecurity, privacy, and resilience to generate reliable results through digital transformation
Security
Service
The shift to digitally-orientated business has driven innovation and has created new value, but businesses leveraging digital technologies are exposed to increasingly sophisticated cyberattacks that pose significant threats to their organization. Also, laws and regulations around the globe related to protecting the privacy of consumers are becoming increasingly strict and complex. The impact of a single attack will go beyond the company’s IT systems, posing a risk to customers and supply chains and threatening their ability to continue business endeavors. Security is no longer just another expense. It must be treated as a strategic investment in fulfilling corporate responsibility.
ABeam Consulting works with clients to take their cybersecurity, privacy, and resilience to the next level, helping them achieve results through digital transformation.
Trends/Challenges
Formulating an all-encompassing cybersecurity strategy/roadmap and steady implementation to increase corporate value
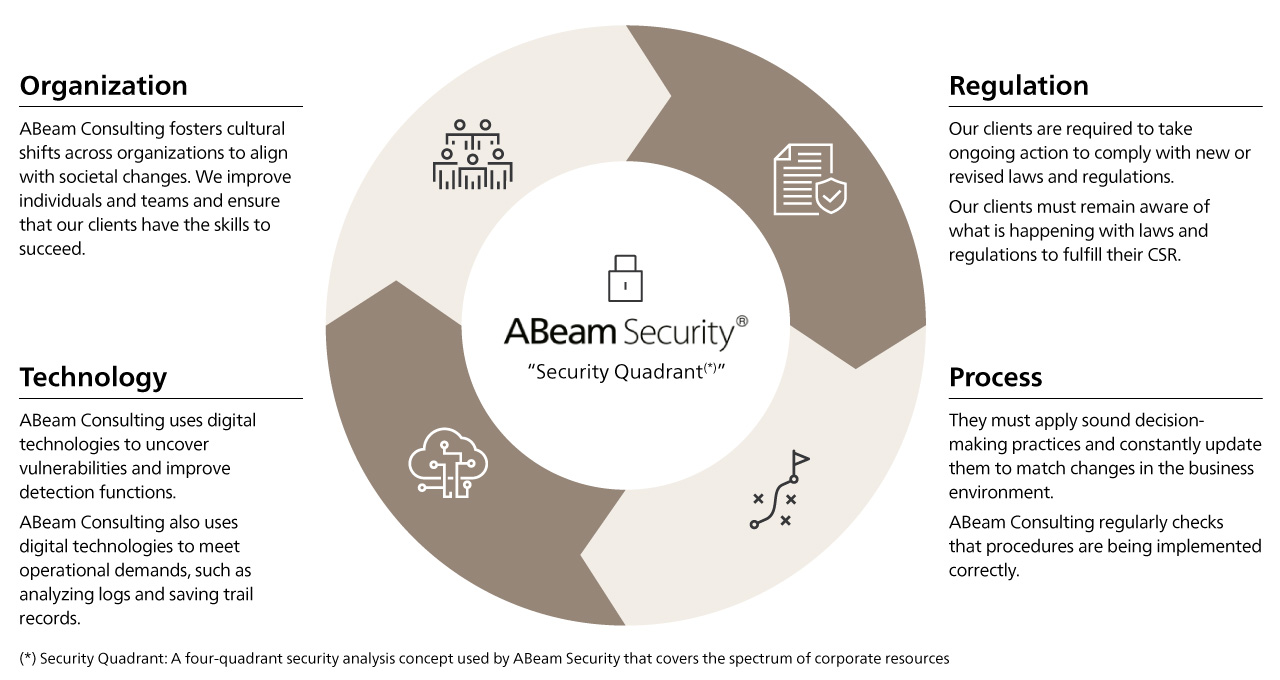
The use and protection of personal and confidential information is essential to the business activities of companies and organizations. However, the increased adoption of digital technologies increases risk as the tools that ensure security become bloated, complex, or obsolete.
The first step is to identify the information assets that should be protected. We then implement measures at the most optimal time and begin enhancing the capabilities of organizations and personnel to maintain and improve these measures. In the next step, it is important to establish and prioritize goals to create a roadmap that navigates each stage of identification, protection, detection, response, recovery, and governance, then plan a future IT architecture and team structure.
Cybersecurity and technology initiatives that drive continuous improvement, education, retention, and advancement of individuals, teams, and operational processes will make it possible to achieve proactive security strategies.

Effective business contingency plans to ensure resilience in the fight against increasingly sophisticated cyberattacks
Completely eliminating the risk of increasingly complex cyberattacks is difficult even with safety measures in place. It is necessary to implement preventive measures to minimize damage and to swiftly recover to continue business operations after an attack. However, business continuity planning (BCP) at many companies is formulated on the assumption of large-scale natural disasters. Companies often have insufficient measures for anticipating serious cyberattack damage, which is far more likely to occur. Unlike downtime caused by a natural disaster, a company that suffers a cyberattack is the sole victim. The impact becomes greater the longer recovery is delayed, resulting in the company losing the trust of society. Companies must formulate measures for their IT systems (recovery environments, data backups, etc.), create comprehensive measures covering both individuals and teams (establishing disaster response protocols, setting business priorities, creating resumption/recovery procedures, etc.), and provide regular training and education.

Addressing data privacy regulations, risks, and strategically using and protecting data
Recent advances in digital technology have made it possible for companies to quickly collect private consumer data. For companies to come out on top, they must explore innovative ways to provide experiences using that data.
However, the use of personal data requires companies to comply with laws and regulations to protect personal information such as the General Data Protection Regulation (GDPR) and to consider the ethics of their practices. There are also other risks that cannot be ignored, such as personal data being collected without consent, interests or details that private individuals want kept secret being presumed, ethical issues involving copyright infringement, discrimination, and prejudice. It is important to identify and reduce privacy infringement risks and to strike the right balance between benefitting from the use of data and protecting that privacy.
A useful approach to protect privacy is to use laws, regulations and trends at other companies as benchmarks to identify issues and to use data by addressing the technical and rule aspects of these issues.

Where ABeam Stands Out
-
One-stop support for everything from security strategy formulation through measure implementation
ABeam Consulting provides all-encompassing support for defining and implementing a roadmap/vision according to the business priority level. We face threats with our clients with our expertise in consulting and cybersecurity.
-
Ongoing assistance for reasonable security governance measures
ABeam Consulting supports corporate governance and security compliance by formulating and investing in reasonable cybersecurity measures tailored to the needs of the client. We also provide ongoing assistance to formulate transparent practices to help clients fulfill their accountability to stakeholders.
-
Using our insights and knowledge of the latest trends to present client-tailored optimal solutions
ABeam Consulting understands the ever-changing security threats of the digital landscape. We can assess available technologies and solutionsto configure the best approaches to suit each client before facilitating their implementation.
Services Provided
ABeam Consulting’s expert insights provide the integrated ABeam Security® solution, which provides practical cybersecurity measures to help our clients achieve the necessary level of security that will help them achieve a digital transformation.
Security Consulting
-
ABeam Security®: Security Maturity Assessment Service (Japanese)
-
ABeam Security®: Support Service for Privacy Law Compliance Assessment and Response (Japanese)
-
ABeam Security®: Security Assessment Utilizing Privacy Data (Japanese)
-
White Hat Cyberattack Risk Diagnostics (Japanese)
-
ABeam Security® Vulnerability Assessment Service (Japanese)
-
Cloud Security Guideline Formulation Support Service (Japanese)
Click here for inquiries and consultations
